- Rogers Community Forums
- Forums
- Internet, Rogers Xfinity TV, & Home Phone
- Internet
- Re: Rogers Hitron CODA-4582 Hardware
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Subscribe
- Mute
- Printer Friendly Page
Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
12-13-2016
11:54 AM
- last edited on
12-14-2016
05:50 PM
by
![]() RogersMaude
RogersMaude
Announced 13-December-2016 by @RogersDave http://communityforums.rogers.com/t5/forums/forumtopicpage/board-id/Getting_connected/message-id/379...
Credit to @Hybrid_Noodle
Hitron website: http://www.hitron-americas.com/product/coda-4582/
Datasheet: http://www.hitron-americas.com/wp-content/uploads/2016/09/CODA-4582-Datasheet.pdf
60W Power Supply built into unit
Pictures of Hardware Version 1A:
***Added Labels***
- Labels:
-
Gigabit
-
HiTron
-
Internet
-
WiFi
-
Wireless Connectivity
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-11-2017 08:56 AM
These are all valid concerns, but all trivia since the issues are with the CODA-4582, please don't confuse the issues. Thanks!
I have not used the DIR 655 in a long while and only connected it to debug the CODA-4582 wireless SMB issue , it is no longer connected and only was for an hour. Its a B and firmware is up to date. no DD-WRT firmware. Other PCs /routers were detected after the Rogers firmware up date a few days ago when they broke the Status->wireless->wireless client feature. That being said the WPS has always been disable on the CODA -4582 wifi's and my pass code is the maximum 36 characters long. There is no way to hack a 36 character AES encripted pass code. The issues are.
1. UPNP on the router is not implemented correctly
2. SMB does not work on the wireless.
3. The Status->wireless->wireless clients crashes the Hitron GUI
4. Windows 10 is able to detect other PCs, routes connected to the network likely on the 2.5GHz WiFi.
Hope this gets us back on track to the issues.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-11-2017 09:19 AM - edited 01-11-2017 09:24 AM
@Datalink wrote:@FATBADCAT did you notice those other routers on your network prior to connecting the DIR-655? I wouldn't think that would be possible, unless the modem has its WPS enabled for either the 2.4 or 5 Ghz networks. Please check the modem settings if you're using the 5 Ghz network and disable the WPS. Reboot the modem if you have to disable the WPS. After the reboot run a check for those other connected devices that are not from your network. WPS is not secure and these days is easily hacked. I'm not sure of whether or not continued access to the modem is possible if a device has connected via WPS and then the WPS function is disabled at some point. I don't believe there is any transfer of the network passphrase to anyone hacking into a modem or router thru WPS, but, thats not to say that the passphrase was not hacked by other means. The passphrase should be random characters, numbers and special characters. Any single term passphrase or common phrase that can be found in a dictionary is susceptible to hacking and can be cracked within seconds or minutes.
As far as the DIR-655, there are three models of that router and the last update for the C Model was in 2014. The A & B models were updated in 2013. So, that router is really out of date, security wise. Its time to park that router and replace it for one that has current, ongoing security updates available. Its too bad that the 655 was never supported by DD-WRT firmware. Its one of the few D-Link routers that DD-WRT does not support.
So, between the modems WPS and the 655, its possible that your network has been hacked, personal opinion.
Just to add the 655 is a known exploitable Router, and there are ways to deauth and brute and or fish, or reave a WPS WPA/WPA2 Key now, which can be done. This combine with habits a lot are guilty of. Using the same SSID and Passphrase when upgrading equipment, so if someone compromised the passphrase on the 655 and you used the same SISID and passphrase on the CODA, it is very possible that the network has been compromised. There really isn’t any other way for unauthorized devices to successfully attach themselves to an AP otherwise.
Further more the DIR-655 ALL revisions sufffer from an exploit that allows a user unautorized access to the Router config so once they gained access they could have easilly gained access to the config and written down your credentials, and if you reused them at any point after that they coudl just get bac on.
Bottom line, the DIR 655 is probably the problem here, and the fact the user states that the connection keeps going up and down on that 655 on rogers suggests that some one in his wifi range is attacking the 655 and deauthing his clients or causing the router to crash reboot to gain access (both known attack methods) to the exploits and unauthorized access.
@FATBADCAT you may also have used the same SSID and passphrase on your cottage 655 for convience as well which also might have added to the situation when you swapped locations. Those Unauthoed devices shwoing up on the CODA might have been from when you connected the 655 as a simple AP they would show on the CODAS device list because the 655 is in passthrough but it doesnt mean the CODA is the point of entry the 655 was/is in this case. And the conneced devices list is also bugged so even after removing the 655 it might have retained those devices in the list.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-11-2017 09:30 AM - edited 01-11-2017 09:31 AM
Forgot to mention "RALINK" chipsets are the go to and very popular wireless chipset when attacking wireless networks, because of the compatibility for pen testing... or nefarious attacks.
I own a few RALINK adapters for testing our networks in Kali linux. WPS and WPA/WPA2 is very exploitable still on some hardware the 655 being in that exploitable list.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-11-2017 01:44 PM
My hard wire come right off the Rogers modem. The wires are fine I have a tester. They only stopped working when I plugged them back into the new modem/router.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-11-2017 04:18 PM
The 2.4GHz hacking could explain the yo-yo back when I was using the DIR-655, rogers could never explain it from the WAN side. The DIR 655 has been permanently retire for a while and no longer an issue.
I will no doubt change the 2.4GHz and 5GHz pass phrase just too be safe on the CODA-4582. I live in suburbia and will start using wireshark to track activity. 2.4G has a limited range of a few houses and I know my close neigbours and kids. None of them are that bright or tecnnical except for the unemployed "Cable Guy" to the rear. I think he has probably taken up a hobbie with all his spare time, since I assume the movie was not far off the mark. I should be able to isolate if the source is 2.4GHz/5GHz or WAN. I still think CODA-4582 has a big hole somewhere. I ve only had it for a week, and all this happened since then. Everything seemed solid with the Hitron CGN3 and no strange computer were showing up. Its been a while since I used the DIR-655 and I don't think he ever got in, just kept crashing it trying to extract a 36 character pass phase which would take forever. Seemed to walk right into the Coda-4582.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-11-2017 04:52 PM
I would suggest you do the same, Factory Reset, then set the security and other settings the way you like.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-11-2017 04:56 PM
@gp-se wrote:I have a WD My Cloud, I also cannot connect to my NAS using Windows Wifi, my MacBook Pro however will connect using Wifi without issue, however I think it's connecting with AFP instead of SMB. My PS4 Pro using LAN cable can connect to the NAS without issue. So it looks like a SMB Wifi issue.
Just an update, I set my MacBook Pro to connect using SMB over WiFi, and I couldn't connect. So this issue is Operating System Indipendant. When I connect using AFP over WiFi it will connect, just no SMB over WiFi. Using my PS4 Pro over LAN I can connect to SMB. Does anyone know if the .20 firmware corrects this? I'm on Network Wide Release .19
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-11-2017 05:11 PM - edited 01-11-2017 05:47 PM
@FATBADCAT hopefully there isn't a security hole in the 4582, but consider this. Hacking into a router or modem is made easier when the SSID and passphrase are single words or commonly used phrases. The two of those are hashed together to form the wifi encryption. These days, those hashed results can be found in files accessible thru the internet, or on CD sets. Various individuals have gone thru the trouble of crunching those two items together, using millions of combinations. So, any combination sourced on common words or phrases can be determined. It doesn't help these days that millions of passwords have been stolen from various websites and possibly added to these lists.
A hacker will transmit a deauthentication command to the router or modem, forcing a device off-line. Then he or she will sit back and record the two way exchange that occurs as the device authenticates and is allowed back on the net. The hacker then takes that recorded exchange and compares the encryption portion to his or her file list. Its a basic pattern match which is a trivial exercise on a pc or laptop. When the pattern is matched, the SSID and passphrase are then known.
Routers on the market these days have a function called Protected Management Frames. This will encrypt the management portion of the 802.11 protocol which at the present time is not encrypted. This is a fairly new step to protect wifi networks and prevent what I described above. Here is one brief explanation of this:
https://www.gigawave.com/2016/05/10/techtip-802-11w-protected-management-frames/
If you run a search for Protected Management Frames, you will see a number of articles on it that are worth reading thru.
Whether or not you can use that function depends on the devices that are on your network. That takes a little homework to see if you can use that for any or all of the connected devices. One other step you can take to protect your network is to use random characters in the SSID and passphrase, and I do mean random. Even if you wanted to use a phrase of some type for the passphrase, consider randomizing the SSID and passphrase using the following site:
https://www.grc.com/passwords.htm
When you refresh that page, the character strings are all changed.
The SSID field is 32 characters long. My recommendation is to fill it completely with a string from that site. Its very rare these days that you actually have to key in the SSID into any device, normally the SSID is detected by the device and selected by the user. So, normally this should be a fairly easy thing to do. What this does is result in a hashed result, combining the totally random character string with your chosen passphrase. That makes a pattern match to any existing file list all but improbable. Thats not to say that a wifi password is impossible to hack. It can be done these days with GPUs, which are designed to run mathematical computation extremely fast. So, no one should be feeling totally smug about their wifi security. Hacking is possible, it just takes longer to do. So, the goal should be to make it so difficult that the hacker will move on to someone else on the street with lesser security. Having a neighbor living behind you with nothing but time on his hands does present a challenge. Best thing you can do is make this extremely hard to carry out.
The one thing that you can't prevent is someone running a deauthentication command for a connected device where that device does not support 802.11w. That is the encryption addition to the Management Frames. For a device that has that capability, and a router that has it enabled, you should be ok, without it, its open season I suspect. It might be possible to capture that command on the router, don't know off the top of my head. If so, then you would know for sure that someone is attempting to hack your network. If this was an ongoing issue, a complaint to the RCMP or Industry Canada might bring about some response.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-12-2017 09:02 AM - edited 01-12-2017 09:05 AM
this new gigabit router is garbage...2 techs told me so and I'm experiencing it. Much better experience with my previous 250 package router. Speeds went from ~300 down to 70...maybe...and flat out stalls on the Download side to about 1 or 2 mbps! Upload is fine but how often do i use that?? Restarting this 3 times a day. I've already had it swapped out for the same router. I'll be going to get it swapped out for an older Ignite model. Yet ANOTHER example of Rogers rolling equipment out waaaay before it's actually ready. Garbage.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-12-2017 10:53 AM
Just as a point, the techs used to call the old routers/modems garbage too. I'd take their opinion with a grain of salt.
@tsac1 wrote:this new gigabit router is garbage...2 techs told me so and I'm experiencing it. Much better experience with my previous 250 package router. Speeds went from ~300 down to 70...maybe...and flat out stalls on the Download side to about 1 or 2 mbps! Upload is fine but how often do i use that?? Restarting this 3 times a day. I've already had it swapped out for the same router. I'll be going to get it swapped out for an older Ignite model. Yet ANOTHER example of Rogers rolling equipment out waaaay before it's actually ready. Garbage.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-12-2017 11:59 PM
I get worse than dial-up speeds for download, but 50Mbps upload. Reset modem, works fine temporarilly. Thinking to go back to the CGN3 😞
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-13-2017 01:06 PM
Took my Hitron CODA-4582 back this morning and swapped for the older Hitron-CNG3 Rocket modem. Life is too short to deal with Roger's messes. May revisit in a year or so, but will check back here first, to see how stable it is (Not!). So long.....
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-13-2017 04:42 PM
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-13-2017 05:47 PM
@soundwave80 wrote:
I'm thinking of doing the same thing. The coda is supposed to have a better processor chip , however it feels like a step backwards. Would of been nice if Rogers opted for another brand all together.
There is no other brand that they can really choose, though. From what I've been able to see, the reason they pick Hitron is because Hitron is fastest to market on a given chipset. It took years for there to be other 24/32 channel Puma 6 DOCSIS 3 modems, and I don't think there are any currently shipping D3.1 Puma 7 DOCSIS 3.1 modems. And Rogers seems to really like being ahead of the curve - they were massively shipping 24-channel CGN3-family modems at a time when US MSOs were barely on 8-channel D3.
I also suspect a lot of the code running on these things come from Intel... and one of the downsides of rushing to market is that fewer bugs in this code have been identified/fixed. If another manufacturer launches their Puma 7 product in a year, that means they'll benefit from almost a year of Intel bug fixes as a result of Hitron/Hitron customers' bug reports...
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-13-2017 06:43 PM
Hooray for my awesome gigabit speeds. Using .19 and it's been like this for the last hour. I have to admit .19 has been ugly at best, I feel like I was better off with .13... Anyone else with this atrocious performance?
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-13-2017 08:10 PM
@gbssengo can you pull the power from the modem and then plug it back in to force a modem restart. If that temporarily resolves the situation, I suspect that @RogersDave will advise you to swap the modem. If you do end up swapping the modem, ensure that the new modem has a black dot on the outside packing box, and at the back of the modem. That signifies that the modem has additional shielding over the Docsis tuner.
Are you running the 2.4 Ghz wifi by any chance?. One more test is to turn off the 2.4 Ghz wifi and rerun the speedtest. If you see the rates return to where they should be, definitely swap the modem.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-13-2017 08:48 PM
@Datalink wrote:@gbssengo can you pull the power from the modem and then plug it back in to force a modem restart. If that temporarily resolves the situation, I suspect that @RogersDave will advise you to swap the modem. If you do end up swapping the modem, ensure that the new modem has a black dot on the outside packing box, and at the back of the modem. That signifies that the modem has additional shielding over the Docsis tuner.
Are you running the 2.4 Ghz wifi by any chance?. One more test is to turn off the 2.4 Ghz wifi and rerun the speedtest. If you see the rates return to where they should be, definitely swap the modem.
@Datalink thanks for the suggestion. I disabled 2.4 Ghz first, and that made no difference.
Did a power cycle, and VOILA! Back to normal. Okay, off to Rogers store for a new modem!
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-13-2017 09:05 PM
@gbssengo, one last check before you head out the door. Can you log into the modem, navigate to the STATUS .... DOCSIS WAN page, copy the Downstream and Upstream tables and paste them into a post. Those are the signal levels for the RG-6 cable. I'd like to make sure that they are ok. A modem restart can temporarily resolve signal levels as well, but it won't resolve any underlying issues such as cable or connector issues.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-13-2017 09:27 PM
@Datalink Information is pasted:
| Port ID | Frequency (MHz) | Modulation | Signal strength (dBmV) | Channel ID | Signal noise ratio (dB) |
| 1 | 669000000 | 256QAM | 2.900 | 19 | 40.946 |
| 2 | 561000000 | 256QAM | 2.300 | 2 | 40.946 |
| 3 | 567000000 | 256QAM | 2.500 | 3 | 40.366 |
| 4 | 573000000 | 256QAM | 2.500 | 4 | 40.366 |
| 5 | 579000000 | 256QAM | 2.800 | 5 | 40.366 |
| 6 | 585000000 | 256QAM | 2.500 | 6 | 40.366 |
| 7 | 591000000 | 256QAM | 2.600 | 7 | 40.366 |
| 8 | 597000000 | 256QAM | 2.200 | 8 | 40.946 |
| 9 | 603000000 | 256QAM | 2.300 | 9 | 40.366 |
| 10 | 609000000 | 256QAM | 2.200 | 10 | 40.366 |
| 11 | 615000000 | 256QAM | 2.100 | 11 | 40.366 |
| 12 | 621000000 | 256QAM | 2.200 | 12 | 40.946 |
| 13 | 633000000 | 256QAM | 3.100 | 13 | 40.366 |
| 14 | 639000000 | 256QAM | 3.000 | 14 | 40.366 |
| 15 | 645000000 | 256QAM | 3.300 | 15 | 40.366 |
| 16 | 651000000 | 256QAM | 3.100 | 16 | 40.366 |
| 17 | 657000000 | 256QAM | 3.100 | 17 | 40.366 |
| 18 | 663000000 | 256QAM | 2.700 | 18 | 40.366 |
| 19 | 555000000 | 256QAM | 2.500 | 1 | 40.366 |
| 20 | 675000000 | 256QAM | 2.800 | 20 | 40.946 |
| 21 | 681000000 | 256QAM | 3.100 | 21 | 40.946 |
| 22 | 687000000 | 256QAM | 2.800 | 22 | 40.946 |
| 23 | 693000000 | 256QAM | 2.800 | 23 | 40.366 |
| 24 | 699000000 | 256QAM | 2.700 | 24 | 40.946 |
| 25 | 705000000 | 256QAM | 2.700 | 25 | 40.366 |
| 26 | 711000000 | 256QAM | 2.300 | 26 | 40.366 |
| 27 | 717000000 | 256QAM | 2.800 | 27 | 40.366 |
| 28 | 723000000 | 256QAM | 2.700 | 28 | 40.366 |
| 29 | 825000000 | 256QAM | 0.700 | 29 | 38.983 |
| 30 | 831000000 | 256QAM | 0.600 | 30 | 38.983 |
| 31 | 837000000 | 256QAM | 0.100 | 31 | 40.366 |
| 32 | 843000000 | 256QAM | 0.200 | 32 | 38.983 |
| Receiver | FFT type | Subcarr 0 Frequency(MHz) | PLC locked | NCP locked | MDC1 locked | PLC power(dBmv) |
| 0 | NA | NA | NO | NO | NO | NA |
| 1 | 4K | 275600000 | YES | YES | YES | 3.900002 |
| Port ID | Frequency (MHz) | Modulation | Signal strength (dBmV) | Channel ID | Bandwidth |
| 1 | 30596000 | ATDMA - 64QAM | 34.000 | 1 | 6400000 |
| 2 | 38595824 | ATDMA - 64QAM | 37.250 | 3 | 3200000 |
| 3 | 23700000 | ATDMA - 64QAM | 32.750 | 2 | 6400000 |
| Channel Index | State | lin Digital Att | Digital Att | BW (sc's*fft) | Report Power | Report Power1_6 | FFT Size |
| 0 | DISABLED | 0.5000 | 0.0000 | 0.0000 | -inf | -1.0000 | 4K |
| 1 | DISABLED | 0.5000 | 0.0000 | 0.0000 | -inf | -1.0000 | 4K |
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
01-13-2017 10:49 PM - edited 01-13-2017 10:50 PM
@gbssengo your signal levels are good, and, you have one OFDM channel operating in Docsis 3.1 mode as well. So, your downloads should be fairly fast. I also wouldn't expect to see any issues with your signal levels. If you still have that modem, and you are experiencing slow data rates, can you post the signal levels again without any modem restart. I'm just wondering what they look like when that happens. There's nothing at the present time to suggest any issues with them.
Re: Rogers Hitron CODA-4582 Hardware
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
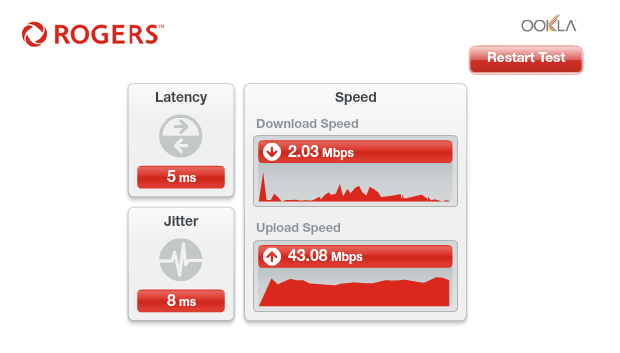
01-13-2017 11:43 PM - edited 01-13-2017 11:49 PM
had a tech come by at approx 4pm tonight...installed the THIRD Coda box (black dot on the box and all) It's 11:38pm and the speeds have slowed down to a crawl (2mb down, 12 up) so I had to restart it. At this point, after having 3 techs, 3 boxes and quite a few calls into tech support, I'm ready to give up on this and just switch to Bell. A few years back I had the Bell 25-10 package and thinking back, that was a dream package compared to the 250(lol) ignite and now this gigabit (LOL) package.