- Rogers Community Forums
- Forums
- Internet, Rogers Xfinity TV, & Home Phone
- Internet
- Re: "Security" levels on XB6 Gateway
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Subscribe
- Mute
- Printer Friendly Page
"Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
12-13-2020 11:58 PM
I had this question buried in a post on a slightly different topic but thought that this was important enough to maybe pull out and ask on its own. Forgive the duplication.
I have set up my new Ignite 500 service and XB6 modem. I have a question that concerns the Security levels of the Firewall under IP4. The default security setting was set to "low" security, so I figured I'd be smart and bump it up to "high" security. All was well until I noticed that every time I do so, I am unable to connect to my Usenet Provider and thought, hmmm.... that can't be a coincidence. I went back into the modem admin settings and reduced the security back to to the "low" default and sure enough, was able to connect to my Usenet service, browsed and downloaded just fine.
I tried "medium" Security and it still connected and downloaded just fine, but as soon as I went back to "high" security, I was unable to connect at all.
So clearly I do not understand what the security levels actually mean, or what they do, in practical terms, but more than anything I wonder in this day and age, why is anything called "LOW" security ever a good default? Anyone care to educate me on why that would be? I thought a major selling point for a good gateway was good internet security....
Re: "Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
12-14-2020 01:50 AM - edited 12-14-2020 02:09 AM
@DrMike When you switch to a higher firewall security level, you add additional restrictions as to what application traffic is allowed to flow through the firewall. Low, Medium and High are not helpful descriptions but Comcast does provide some additional high-level information on the following support page: https://www.xfinity.com/support/articles/advanced-xfinity-wireless-gateway-features
They describe the security levels as follows:
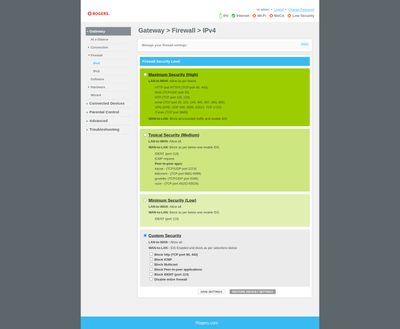
- Maximum Security (High), which will block most applications except web browsing, email, iTunes and VPN.
- Typical Security (Medium), which allows access to most sites and services, but blocks all peer-to-peer applications.
- Minimum Security (Low), which enables all secure apps. This is the default setting when you first use your Wireless Gateway.
- Custom Security, which will allow you to block individual types of traffic, or disable your firewall entirely.
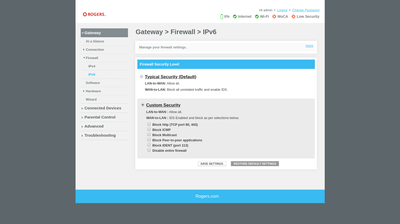
You can also expand the firewall security levels on the XB6 to reveal the following:
My biggest complaint about the XB6's firewall is that the UI will not allow you to see the actual firewall rules that are in place. Furthermore, if you should run into a problem with your VPN not working or your VoIP ATA losing registration, there is no way for you to fix it. You cannot add, remove or change any individual firewall rules. The only Firewall troubleshooting resources available to you are Troubleshooting > Logs: Firewall Logs.
Rogers also has additional firewall rules in place that are not visible to us. They enable Rogers to, for example, poll the status of your Ignite set-top boxes... and who knows what else.
So clearly I do not understand what the security levels actually mean, or what they do, in practical terms, but more than anything I wonder in this day and age, why is anything called "LOW" security ever a good default? Anyone care to educate me on why that would be? I thought a major selling point for a good gateway was good internet security....
The "Low" security level setting provides basic protection from outside attacks and (hopefully) should not break any of your applications. It does not restrict you from using any applications and it blocks random incoming connections from the Internet. This is similar to the default behaviour that you would see on the firewall of a typical consumer router.
Re: "Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
12-14-2020 07:57 AM
My biggest complaint as well is not seeing the details of the firewall rules.
Re: "Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
12-14-2020 11:02 AM
I decided on "Medium" aka Typical Security for now. Seems to be working OK for the sites I visit and the apps etc I use.
What baffled me more was the unhelpful labels. If "Medium" is defined as being for "typical" usage, why is that not the default? Instead "low" - labelled as "Minimum Security" is the default. I realize that "minimum", doesn't mean "no security", but just calling it "Low" and "Minimum" says to me that this should NOT be the default. On what planet does that make sense?
Sigh......
Re: "Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
12-15-2020 07:42 AM
Re: "Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
04-14-2023 07:17 AM
I have a specific question: Where and how do I close the "wannacry" ports TCP 445 and 139, and UDP ports 137-138?
NB: this isn't because I fear wannacry so much as I want to protect public shares, but protection from that particular exploit is important nonetheless.
Not a Rogers employee, a retired employee within ICSU, Brampton.
Re: "Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
04-16-2023 08:09 AM
Greetings @token!
I regret to inform you that there is no way to manually close specific ports on our modem.
Regards,
RogersCorey
Re: "Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
04-19-2023 03:27 PM
Thanks Corey.
Comcast seems full of surprising little nuggets in their designs, don't they. Having worked directly with them, and Arris & Technicolor on the XB6 vulnerability testing, I'm sorry that we didn't look further into the usability of the darn things.
Re: "Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
04-19-2023 04:12 PM
@token What is the specific security policy that you want to implement? By default, even the lowest firewall setting should block any attempts to connect to those ports from the Internet. By enabling Advanced Security, Rogers claims that this will also provide you with additional "intelligent around-the-clock protection against cyberthreats for your connected home."
However, your biggest threats come from unsafe computing practices within your own home, and no firewall can guard against what may happen when downloading/installing infected software or connecting to an unknown malicious web site.
Re: "Security" levels on XB6 Gateway
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Content
04-19-2023 04:33 PM - edited 04-19-2023 04:42 PM
Thanks for the reply, G.
The gateway provides a firewall between the Internet and my extranet where lives IoT devices such as goog home, entertainment and a separate guest network, My own firewall is the barrier between that extranet and my intranet where I work and play. Previously I allowed no windows fileshare protocols on the intranet--using only Linux systems for myself and my work laptop which is always Windows of course.
But I've built a gaming PC, dual boot with Ubuntu and Windows, and have decided to use a raspberry Pi to share files among the various systems on the intranet. I have a Synology NAS also on the intranet with one port to the extranet gateway for external access, but want a simpler drag-and-drop file sharing solution now, not web-based.
The raspberry Pi has a public writable folder, authentication required, but I don't want it exposed to the web, only intranet so just wanted to ensure no SMB protocols were allowed through the gateway.
Hope that makes sense. I've worked in cyber for a few decades.
PS I was told t by Rogers to disable the advanced security since it interferes with many device functions including the STB.